In the context of increasingly prevalent remote work, cloud computing, and distributed data systems, traditional security models are no longer sufficient. Zero Trust has emerged as a modern security approach, enabling enterprises to govern and protect data more effectively in today’s complex digital environments.
Challenges of Cloud Computing
In the cloud computing era, data and applications are accessed across multiple platforms, devices, and locations, making traditional security boundaries increasingly blurred. As remote and hybrid work models become the norm, perimeter-based security mechanisms that rely on network location are no longer adequate for controlling system access. A single compromised account or a device that fails to meet security requirements can rapidly escalate the risk of intrusion and lateral movement within cloud infrastructures.
Zero Trust has therefore become a critical approach, allowing organizations to enforce strict access controls based on identity and usage context. This helps mitigate risks of data leakage, operational disruption, and compliance issues in complex cloud environments.

What is Zero Trust?
Zero Trust, or Zero Trust Architecture, is a security model built on the principle of “never trust, always verify.” It assumes that no user, device, or application, whether inside or outside the network perimeter should be trusted by default. Instead of treating the internal network as a secure zone, Zero Trust requires continuous verification of every access request based on identity, authorization, and contextual factors. This approach is particularly well-suited for modern enterprises, where data is accessed from diverse locations, devices, and platforms.
Core principles of Zero Trust in Data Governance
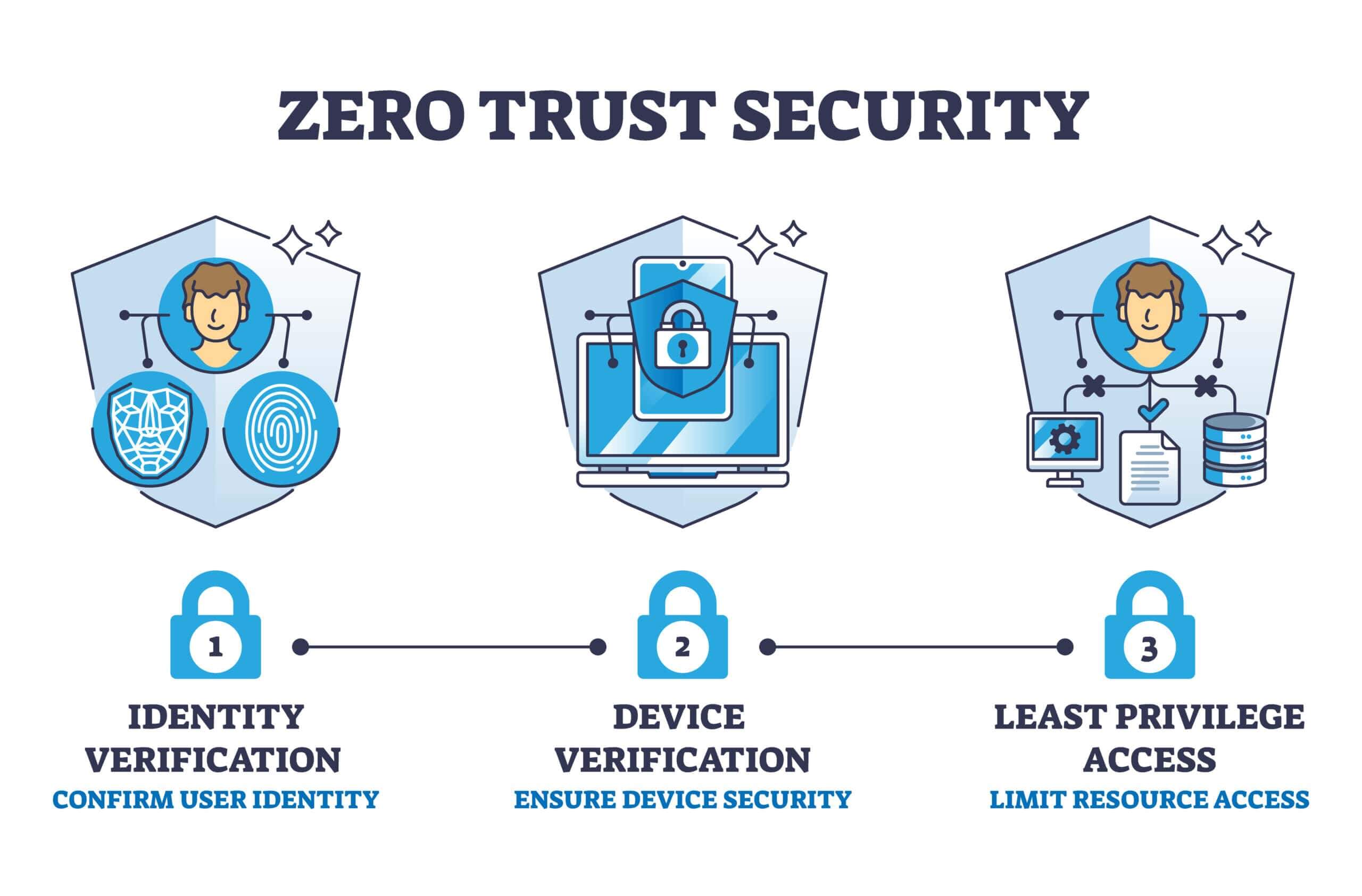
1. Continuous verification
Zero Trust mandates that every access request must be continuously verified, regardless of the user’s location or prior authorization. Each attempt to access data or applications is evaluated in real time based on identity, device posture, and contextual conditions. This approach enables organizations to detect abnormal access behaviors early and prevent risks at the entry point, rather than reacting only after incidents have occurred.
2. Least privilege access
The principle of least privilege ensures that users and systems are granted only the access rights necessary to perform their assigned roles and tasks. By limiting access scope, organizations can significantly reduce the potential impact of security incidents and minimize the risk of misuse or abuse of sensitive data. This principle serves as a fundamental pillar for effective data control in complex environments.
3. Microsegmentation
Microsegmentation divides systems into isolated segments, each governed by its own access policies, rather than operating within a single trusted zone. When one component is compromised, attackers are unable to move freely across the environment, thereby limiting lateral movement and privilege escalation. This principle helps isolate risks and enhance control in large-scale cloud systems.
4. Data-centric security
Zero Trust places data at the center of the security strategy, focusing on protecting data in all states whether at rest, in transit, or in use. Through data classification, access control, and the application of appropriate protection mechanisms, organizations can ensure that critical data remains secure, even if other security layers are breached.
The importance of Zero Trust for enterprises
In cloud environments, traditional perimeter-based security models are no longer effective, as data and applications are no longer confined within fixed boundaries. By leveraging continuous verification and least privilege access, Zero Trust enables enterprises to:
- Protect data when network perimeters are no longer clearly defined by shifting the security focus to access control and data protection at every connection point.
- Prevent unauthorized access early through continuous verification of identity, device, and contextual factors.
- Minimize the impact of security incidents by ensuring users can access only the specific data they need.
- Securely support remote and hybrid work environments with consistent access control regardless of user location or device.
- Meet compliance and data governance requirements through clear access policies and continuous monitoring that enhance transparency in data usage.
A clear understanding and systematic implementation of Zero Trust provide a solid foundation for enterprises to fully leverage the benefits of cloud computing without compromising on security.



